OPNSense and Wireguard
After investing some time to successfully set up Wireguard in OPNsense, I would like to share some screenshots of my test setup here. In this configuration, I used OPNsense exclusively as a VPN server and deliberately omitted the WAN interface. For testing purposes, OPNsense was installed on a HyperV server. A prerequisite for the setup is port forwarding for port 51820 on the router to the IP address of the OPNSense installation and a public IP address, see: Making available from the Internet: Port forwarding - OpenWRT.
Download and installation of OPNSense
The download link for OPNsense is here available.
After downloading OPNsense, burn the ISO file to a USB stick or CD. In the computer's BIOS, change the boot order to boot from this media and then follow the installation instructions. After successful installation, I used the following settings:
Network settings
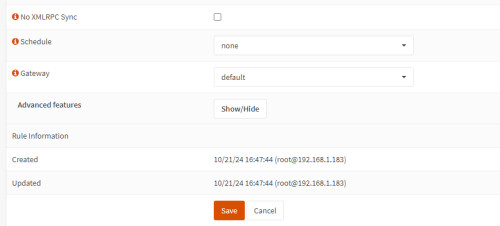
If a DHCP server is already used in the existing network, the OPNSense DHCP server should be deactivated:
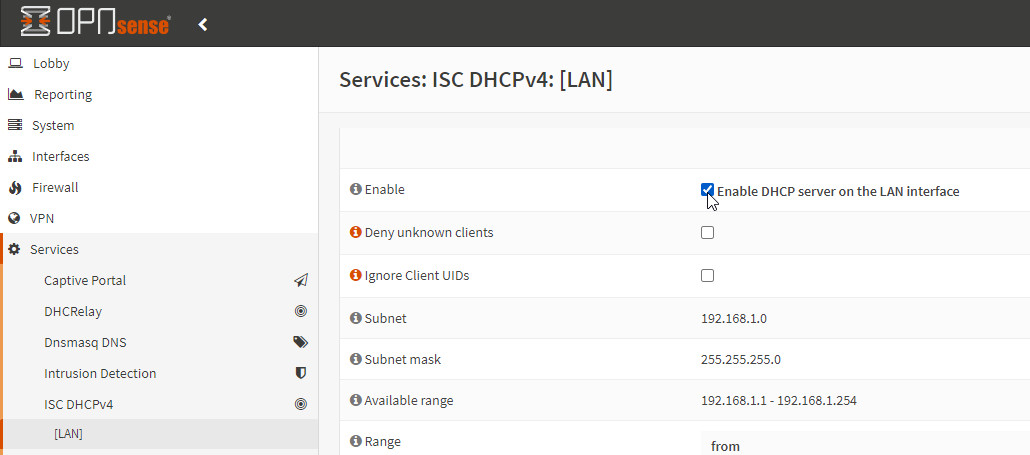
Checkmark for "Enable" should of course be removed.
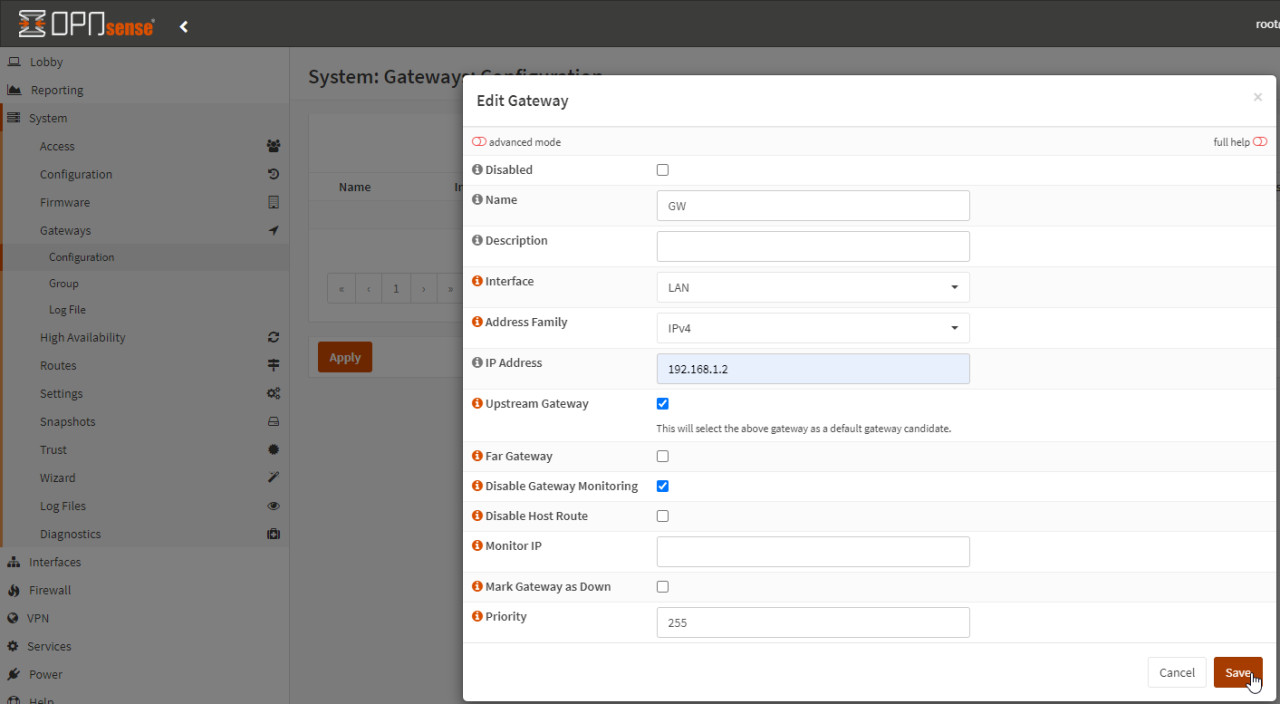
The IP address of the router is required for OpenSense to be able to find its way to the Internet. Menu: "System" / "Gateways" / "Configuration":
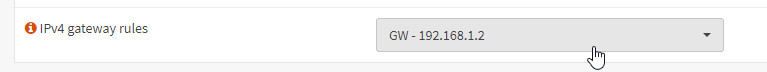
The gateway can then be used in "Interfaces" / "LAN":
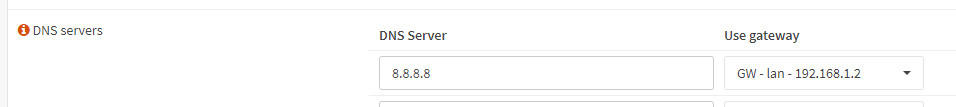
For name resolution, I have added the Google DNS: "System" / "General DNS":
WireGuard-Instance
WireGuard can be activated in OPNSense simply by adding an instance:
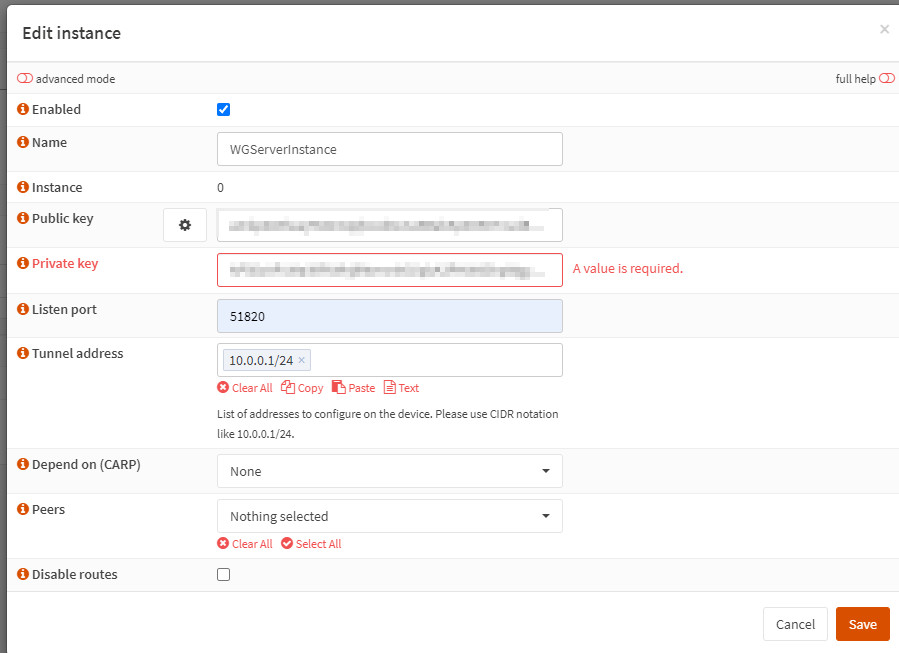
"Generate new keypair" is used to generate a public and private key for WireGuard.

Port forwarding, access from the Internet
Port forwarding to the IP address of OPNSense is required on the router: Port 51820, see: Making available from the Internet: Port forwarding - OpenWRT. Access from the Internet is via the public IP address of the Internet access, see also: Display your own public IP - what is my IP address?
Create clients
Several clients can then be created for access; the public IP address of the Internet access is used as the endpoint:

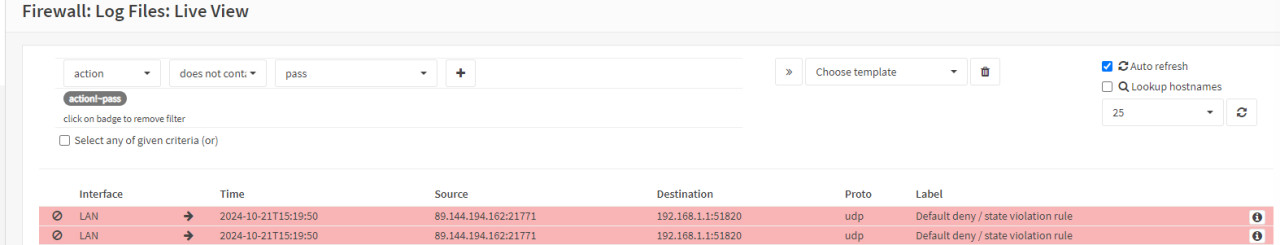
After scanning the QR code with the WireGuard Android app, the app creates a connection profile. Provided the port forwarding has been set up correctly, the connection attempt is now listed in OPNSense in the firewall:
Firewall / Customizations
The live view of the firewall log files now shows us which connections are being blocked. As can be seen in the following screenshot, the OPNSense firewall prevents a connection to the WireGuard instance:
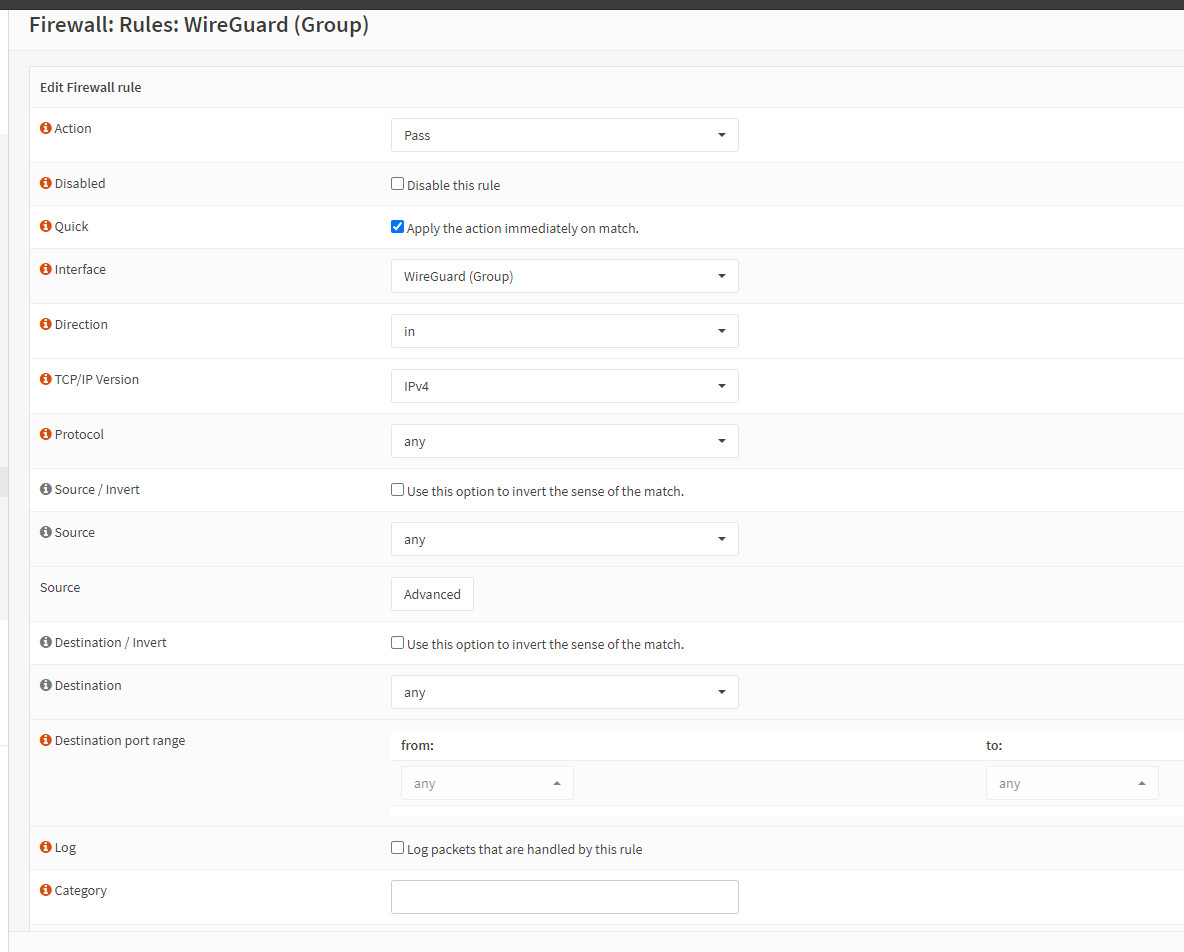
OPNSense requires a firewall rule for the incoming connection from the Internet at this point:
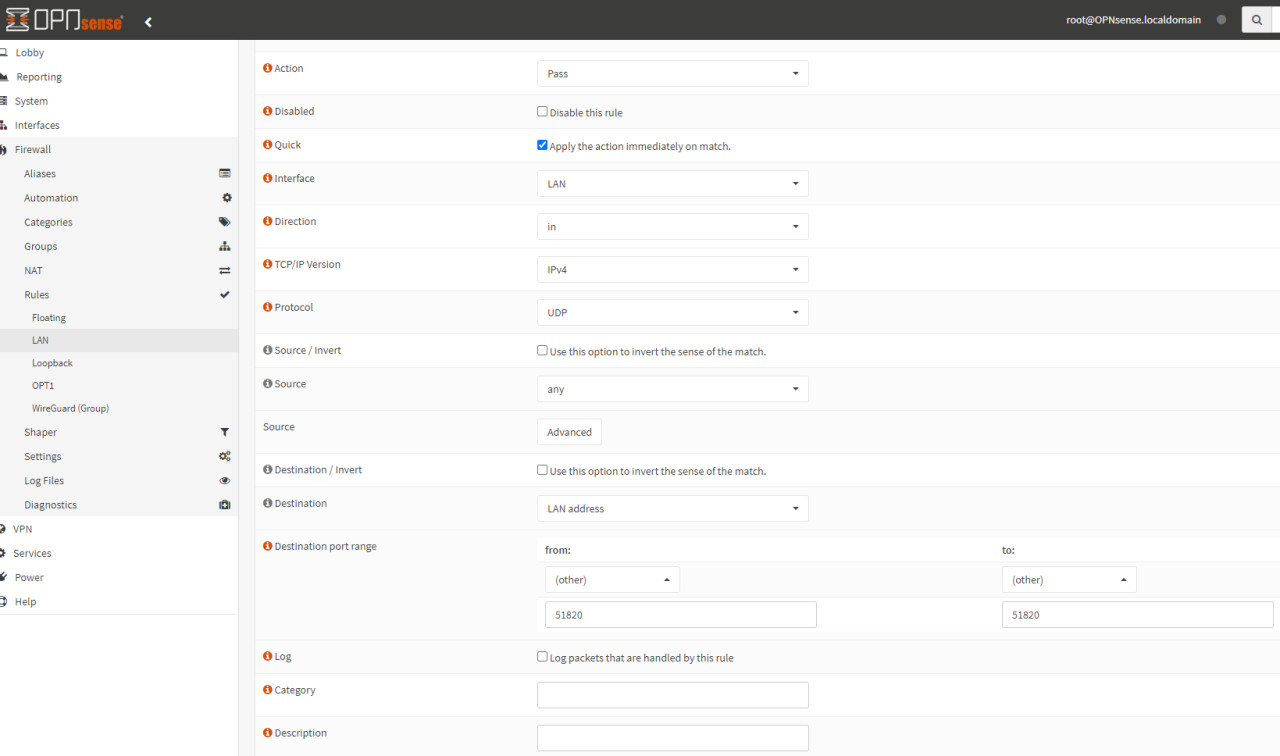
In addition, a rule for access to the internal network is now missing:
Conclusion
Setting up WireGuard on OPNsense as a VPN server without a WAN interface shows how flexible and adaptable OPNsense is. The test setup on a HyperV server demonstrates the possibility of using OPNsense in virtual environments. The necessary port forwarding via the router and the adaptation of the network and firewall settings are crucial to enable access from the Internet. The OPNsense firewall provides the necessary control to monitor and regulate connections. Overall, using OPNsense for WireGuard is a powerful solution for secure VPN hosting.
 ({{pro_count}})
({{pro_count}})
{{percentage}} % positive
 ({{con_count}})
({{con_count}})