Virtual desktop in Docker + Internet browser access
Now I really no longer need a VPN tunnel to my own home network: A desktop infrastructure (CDI) allows me to access a virtual Linux workspace in my own network directly from a browser: Provided via a container.
Docker Basics
Docker allows applications to be launched by command in a so-called container.A container is an isolated environment independent of the operating system (OS):
When a container is first launched, Docker independently loads all the necessary sources
from the internet.
Docker can be installed on Windows, macOS or an Linux Distribution
A simple docker run command is enough to start and the desktop can be reached via the browser with port 6901:
sudo docker run --rm -it --shm-size=512m -p 6901:6901 -e VNC_PW=password kasmweb/desktop:1.15.0To ensure that Kasm Desktop is can be reached securely from the Internet, I use a Let's Encrypt reverse proxy. At first I used Nginx as Reverse-Proxy, but later replaced it with Traefik. The reverse proxy provides an encrypted HTTPS connection and makes it possible to run multiple websites on one server.
Step by step Kasm Desktop and Docker including access from the internet
Hardware requirement:- Almost any hardware can be used for the Docker installation. For example, a virtual server of a provider, or for home: a Mini-PC, notebook, MAC, a NAS: QNAP, Synology or any other hardware with x68-64 architecture on which Windows or Linux can be installed.
- Own registered domain, see domain and its management.
- Cloudflare or Reverse Proxy:
- Cloudflare Tunnel Service or alternatively:
- Port forwarding and Reverse proxy with Let's Encrypt certificate
- '--serverstransport.insecureskipverify'Docker-Compose YAML with access via the Internet
version: "3.8"
services:
kasmweb:
image: kasmweb/desktop:1.15.0
#Labels für ReverseProxy, siehe: https://www.libe.net/traefik
labels:
- "traefik.enable=true"
- "traefik.http.routers.workspace.rule=Host(`workspace.domain.tld`)"
- "traefik.http.routers.workspace.entrypoints=web"
- "traefik.http.routers.workspace.entrypoints=websecure"
- "traefik.http.routers.workspace.tls=true"
- "traefik.http.routers.workspace.tls.certresolver=myresolver"
- "traefik.http.services.workspace.loadbalancer.server.scheme=https"
- "traefik.http.services.workspace.loadbalancer.server.port=6901"
- "traefik.http.routers.workspace.middlewares=forward-auth-verify"
volumes:
- ./profile:/home/kasm-user
shm_size: '1g'
restart: always
environment:
- VNC_PW=password
expose:
- "6901"
#Für einen direkten Test-Zugriff, in den folgenden 2 Zeilen "#" entfernen. Aufruf: http://localhost:83 oder http://ServerIP:83
ports:
- "6901:6901"
#Ohne dem Einsatz eines Reverse Proxy (https://www.libe.net/traefik) fehlt voraussichtlich das Netzwerk webproxy
#und die folgenden Zeilen können entfernt oder auskommentiert werden. Alternativ kann das Netzwerk mit "docker network create webproxy" erstellt werden
networks:
default:
external:
name: webproxyThe file does not use volumes, but subfolders below the docker-compose.yml file. See: Storing Docker data: Docker volumes vs. host folders. In addition to the user name and password, I use a Google account login to access the file from the Internet. A separate middleware is responsible for this, which is interposed via the label: "traefik.http.routers.workspace.middlewares=forward-auth-verify". See: Traefik and oAuth: Log in your own web services with Google.
Start - docker compose up
In the example, the profile data is redirected to a persistent folder. As a prerequisite, this must be created before the actual start:
mkdir profile
sudo chmod 777 ./profile/ -R
docker compose up -d
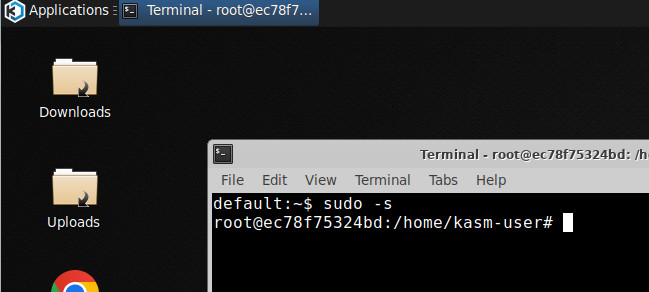
Root permissions
In order to be able to switch to the root account in the desktop without a password, I have extended the Docker image as described in the documentation:
additional file: Dockerfile (without extension), content:
FROM kasmweb/desktop:1.15.0
USER root
ENV HOME /home/kasm-default-profile
ENV STARTUPDIR /dockerstartup
ENV INST_SCRIPTS $STARTUPDIR/install
WORKDIR $HOME
######### Customize Container Here ###########
RUN apt-get update \
&& apt-get install -y sudo \
&& echo 'kasm-user ALL=(ALL) NOPASSWD: ALL' >> /etc/sudoers \
&& rm -rf /var/lib/apt/list/*
######### End Customizations ###########
RUN chown 1000:0 $HOME
RUN $STARTUPDIR/set_user_permission.sh $HOME
ENV HOME /home/kasm-user
WORKDIR $HOME
RUN mkdir -p $HOME && chown -R 1000:0 $HOME
USER 1000Source:
- kasmweb.com/docs/latest/how_to/building_images.html and
- kasmweb.com/docs/latest/how_to/running_as_root.html
The customized image can then be used for the build / start in the docker-compose.yml file:
Contents docker-compose.yml file:
version: "3.8"
services:
kasmweb:
container_name: kasmweb-desktop
build:
context: ./
dockerfile: Dockerfile
#Labels für ReverseProxy, siehe: https://www.libe.net/traefik
labels:
- "traefik.enable=true"
- "traefik.http.routers.workspace.rule=Host(`workspace.domain.tld`)"
- "traefik.http.routers.workspace.entrypoints=web"
- "traefik.http.routers.workspace.entrypoints=websecure"
- "traefik.http.routers.workspace.tls=true"
- "traefik.http.routers.workspace.tls.certresolver=myresolver"
- "traefik.http.services.workspace.loadbalancer.server.scheme=https"
- "traefik.http.services.workspace.loadbalancer.server.port=6901"
- "traefik.http.routers.workspace.middlewares=forward-auth-verify"
shm_size: '1g'
restart: always
volumes:
- ./profile:/home/kasm-user
environment:
- VNC_PW=???
expose:
- "6901"
#Für einen direkten Test-Zugriff, in den folgenden 2 Zeilen "#" entfernen. Aufruf: http://localhost:83 oder http://ServerIP:83
ports:
- "6901:6901"
#Ohne dem Einsatz eines Reverse Proxy (https://www.libe.net/traefik) fehlt voraussichtlich das Netzwerk webproxy
#und die folgenden Zeilen können entfernt oder auskommentiert werden. Alternativ kann das Netzwerk mit "docker network create webproxy" erstellt werden
networks:
default:
external:
name: webproxyPossible clients
To use Debian, for example, only the image in the Docker-compose file needs to be replaced:
version: "3.8"
services:
kasmweb:
..
image: kasmweb/debian-bookworm-desktop:1.15.0
..Or when using the Dockerfile, the From command at the beginning of the Dockerfile:
FROM kasmweb/debian-bookworm-desktop:1.15.0
...Conclusion
As an alternative to VPN access and a remote connection to an existing physical or virtual client, a CDI (Container Desktop Infrastructure) can be used to enable access to a desktop interface within your own network. Compared to virtual servers or clients, a container-based desktop is more resource-efficient and can therefore be operated quickly on hardware that may already be available. See also: Inexpensive and economical Docker Mini Server for the home.
 ({{pro_count}})
({{pro_count}})
{{percentage}} % positive
 ({{con_count}})
({{con_count}})
