Step by step: IPSec VPN Server 2022
This blog entry provides instructions for setting up a secure VPN on a Windows 2022 server. The aim is to set up a VPN with IKEv2 protocol including root CA and certificate. The post contains screenshots and step-by-step descriptions for installing the necessary server roles, certificates and configuring the VPN and NPS server.
Voraussetzung
Prerequisite
Public domain and DNS entry on the public IP address of the Internet access: e.g. for the example domain "domain.tld" a DNS A record on "vpn.domain.tld", see:
- Website construction kit vs. web space or your own web server? and
- display your own public IP - what is my IP address? and
- make available from the Internet: Port forwarding - OpenWRT
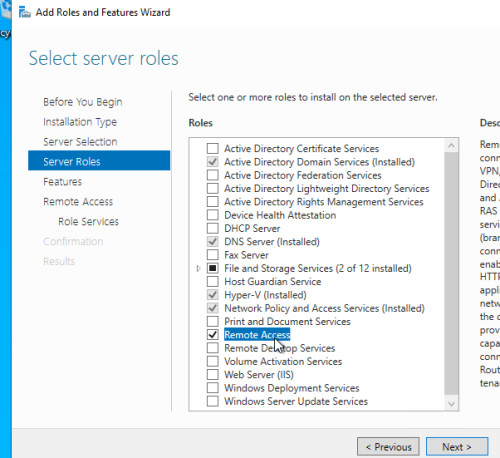
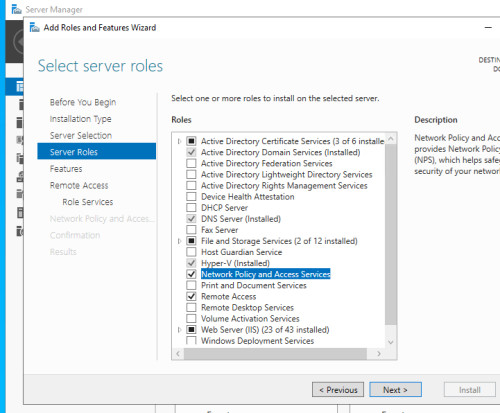
Server roles
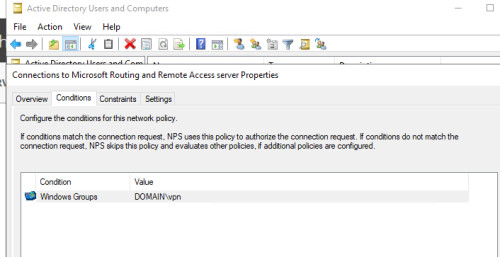
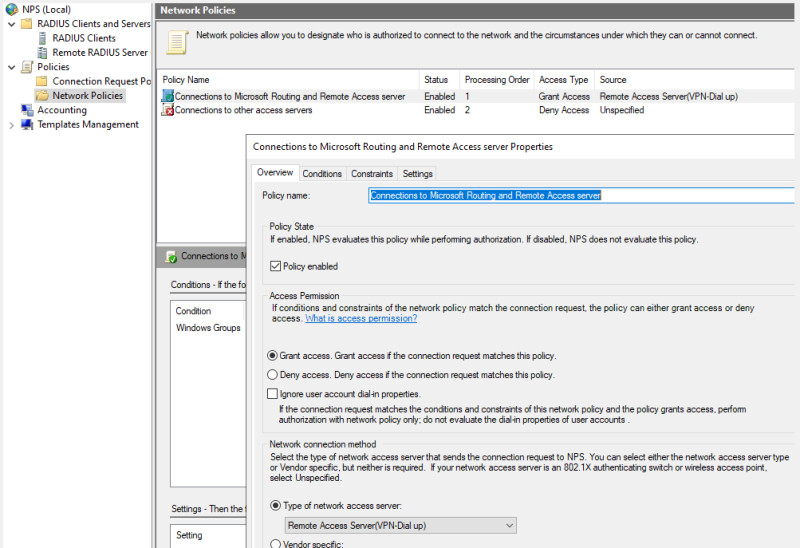
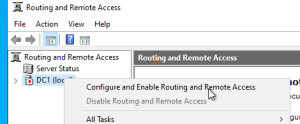
For VPN access via IKEv2, the roles "Remote Access" and "Network Policy and Access Services" as well as the Active Directory certificate services are required.
Set up the certification authority (CA).
Once the certification authority has been set up, a certificate is required. To ensure compatibility with IKEv2, we first need a template.
Certificate management: Manage Templates
As the basis for the IKEv2 VPN certificate, I copy the IPSec template and adapt it as follows:

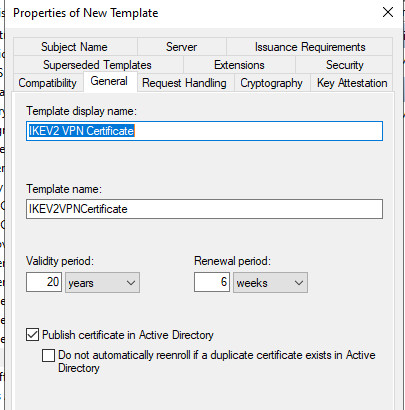
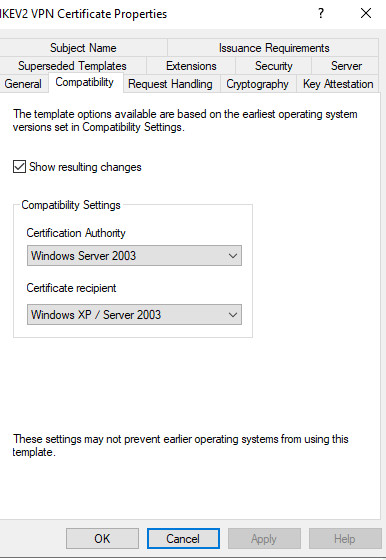
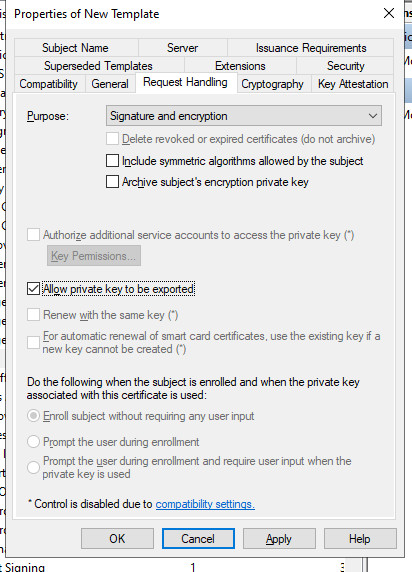
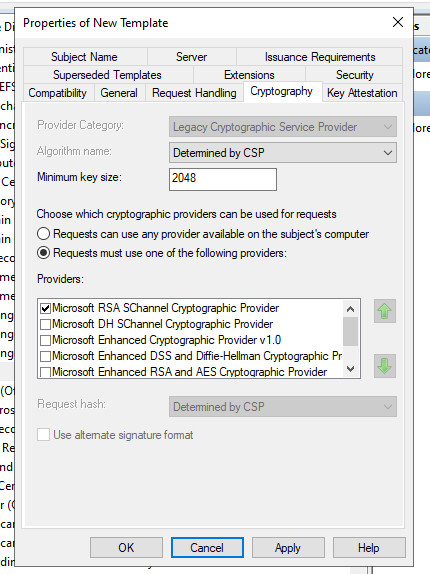
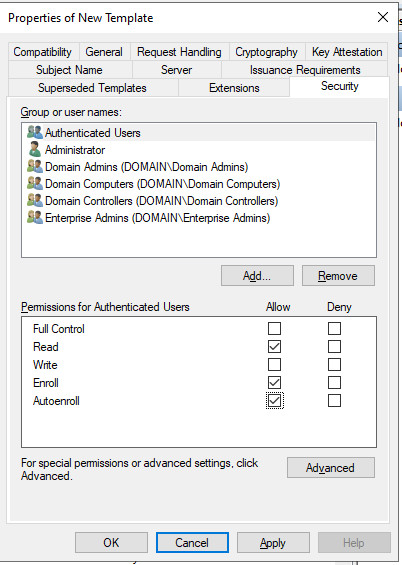
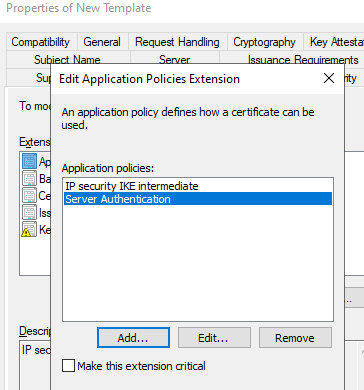
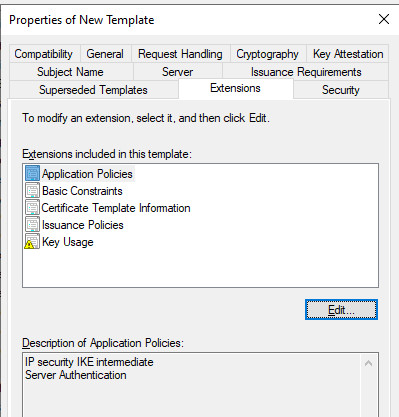

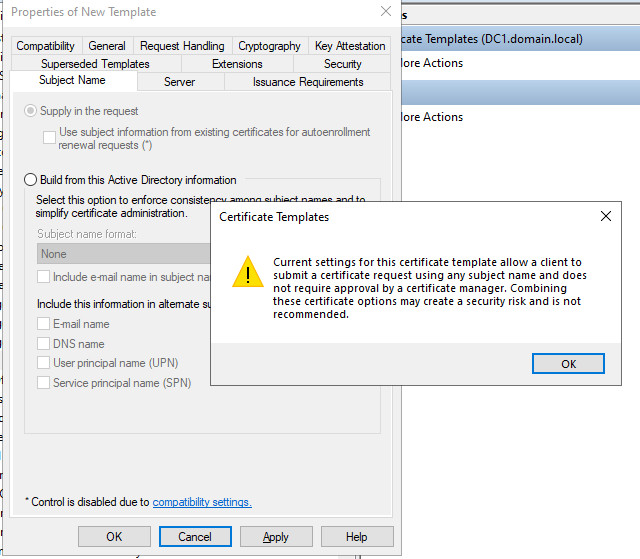
Certificates with a validity longer than 2 years?
To give the certificate a validity period longer than 2 years, I increase the maximum age of certificates for the certification authority to 10 years:
Command in the command prompt:
certutil -setreg ca\ValidityPeriodUnits 10Back in certificate management, I add the previously created template to the available certificate templates:
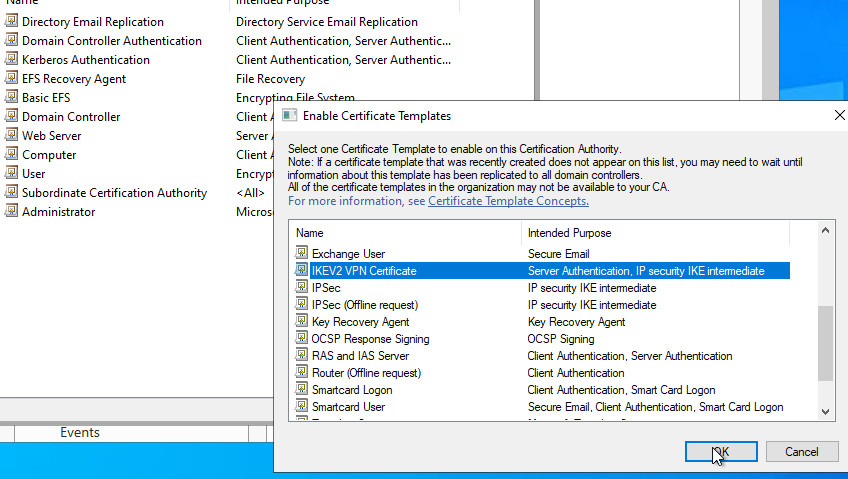
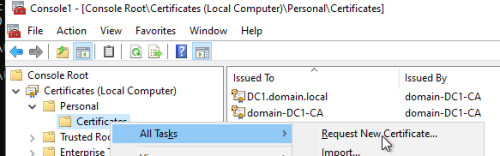
Issue certificate: Request
On the basis of the previously created template, the mmc.exe, Add Snap-In: Certificates: Computer:
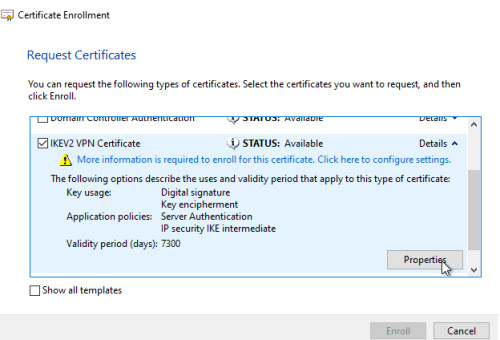
Request New Certificate
I use the previously created DNS entry as the "Common name".
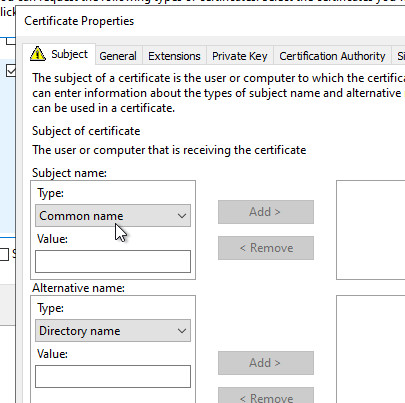
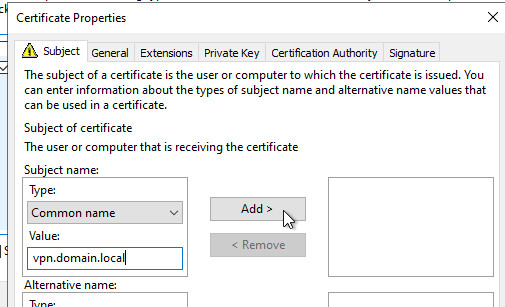
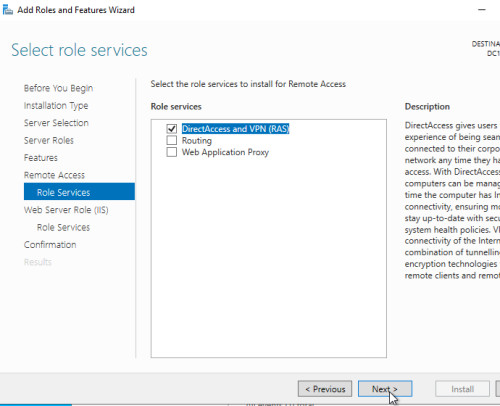
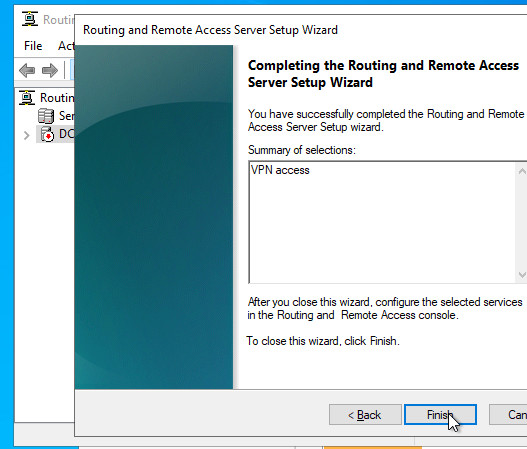
Set up VPN:
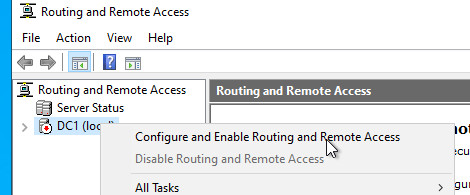
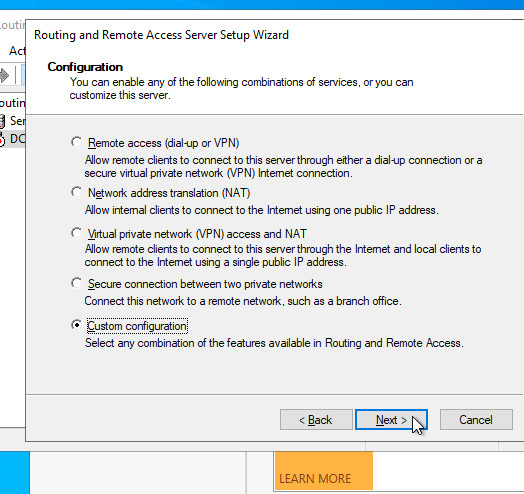
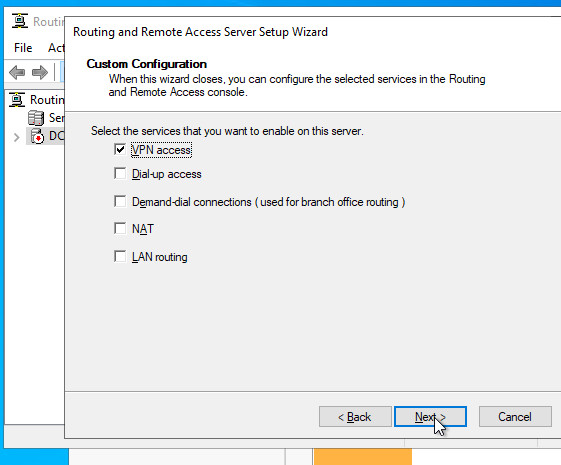
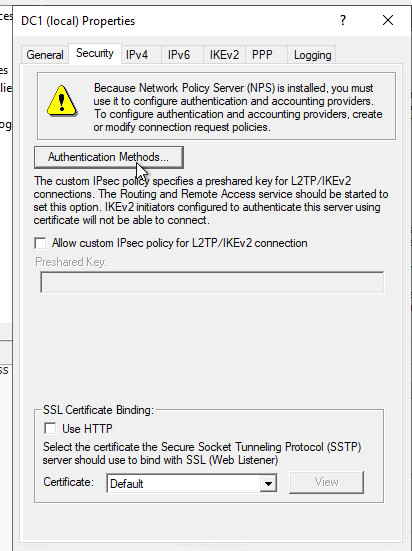
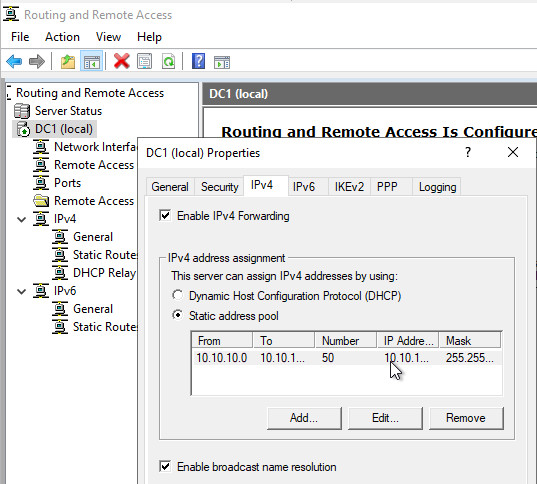
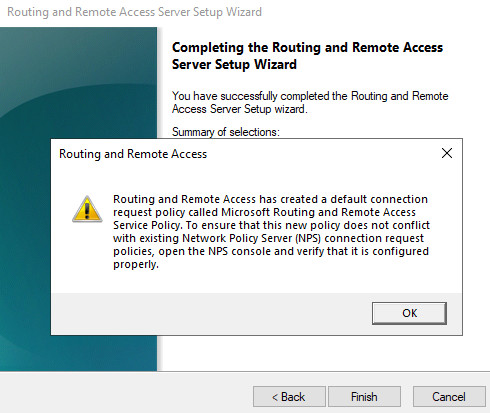
VPN Ports
An dieser Stelle sollten nur die notwendigen VPN-Ports aktiviert werden: am besten alle Ports außer IKEv2.
NPS (Network Policies) service
Port forwarding
To forward VPN requests to the server via the router, port forwarding of the UDP ports 500 and 4500 to the IP address of the server is required, see: make available from the Internet: Port forwarding - OpenWRT
VPN client: Requirements and configuration
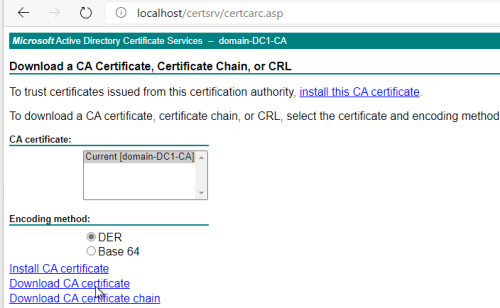
Clients that are in the domain automatically receive the root certificate required for the connection. To connect a client without domain membership, the root certificate can be exported and imported at the client. The easiest way to export the certificate is to use the web service of the certification authority:
SplitTunnel / Networks
The following Powershell line informs the VPN client that the Internet data traffic should be accessed directly and not via the VPN tunnel:
Set-VpnConnection "VPN Connection Name" -SplitTunneling $true
Add-VpnConnectionRoute "VPN Connection Name" 192.168.0.0/16existing VPN profiles can be exported from the following path: %appdata%\Microsoft\Network\Connections\Pbk
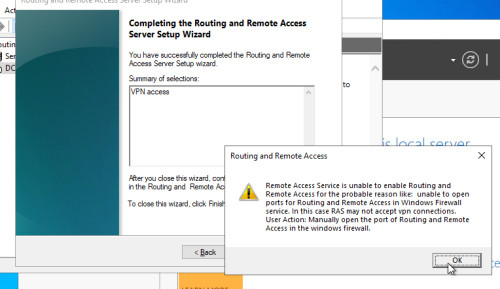
Server: Fehlersuche
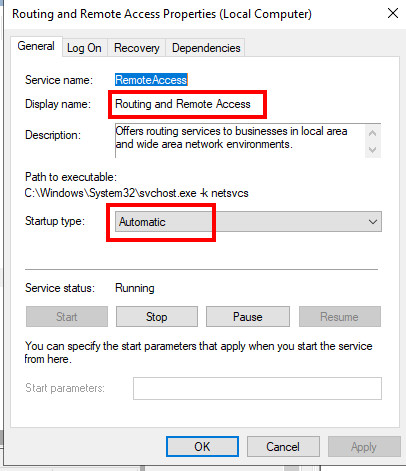
Event ID: 7024 The Routing and Remote Access service terminated with the following service-specific error:
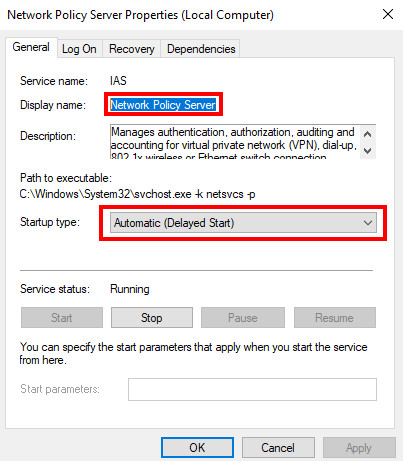
The callback function must be invoked inline. If the Network Policy Server (NPS or IAS) starts faster than Routing and Remote Access (RemoteAccess), the following event is listed and the Routing and Remote Access service does not start.
Solution: Remove Delayed Start for Routing and Remote Access and add it for the Network Policy Server (For NPS, Startup type should be set to Automatic (Delayed Start):
Conclusion
This blog entry provides instructions on how to set up a secure VPN with IKEv2 on a Windows 2022 server. It explains how to correctly configure the server roles, certificates and the NPS server. With a step-by-step description and helpful screenshots, a stable VPN service can be set up without any problems.
 ({{pro_count}})
({{pro_count}})
{{percentage}} % positive
 ({{con_count}})
({{con_count}})