Operate WireGuard VPN server in Docker
WireGuard is an efficient way to enable VPN connections in a Docker container. Docker Basics
A container is an isolated environment independent of the operating system (OS):
When a container is first launched, Docker independently loads all the necessary sources
from the internet.
Docker can be installed on Windows, macOS or an Linux Distribution
docker-compose.yml
The provided docker-compose file defines two main services:
- WireGuard: Uses the "linuxserver/wireguard" image and is responsible for the main VPN connection. The container receives network management rights (NET_ADMIN) and binds volumes and ports for configuration.
- WireGuard UI: Provides a user-friendly web interface to manage the WireGuard connections. This service is dependent on the WireGuard service and operates in the same network mode, allowing seamless interaction. Various environment variables are used to define environment parameters and logging is optimized to limit the log file size.
version: "3"
services:
wireguard:
image: linuxserver/wireguard:v1.0.20210914-ls7
container_name: wireguard
cap_add:
- NET_ADMIN
volumes:
- ./config:/config
ports:
- "5001:5000"
- "51820:51820/udp"
wireguard-ui:
image: ngoduykhanh/wireguard-ui:latest
container_name: wireguard-ui
depends_on:
- wireguard
cap_add:
- NET_ADMIN
network_mode: service:wireguard
environment:
- SENDGRID_API_KEY
- EMAIL_FROM_ADDRESS
- EMAIL_FROM_NAME
- SESSION_SECRET
- WGUI_USERNAME=admin
- WGUI_PASSWORD=password
- WG_CONF_TEMPLATE
- WGUI_MANAGE_START=true
- WGUI_MANAGE_RESTART=true
logging:
driver: json-file
options:
max-size: 50m
volumes:
- ./db:/app/db
- ./config:/etc/wireguardAfter starting with the "docker compose up" command, WireGuuard UI can be accessed via the IP address of the host with port 5001, e.g. http://localhost:5001, if Docker is running on the same machine. The initial password can be specified in the docker-compose.yaml file and changed in the UI.
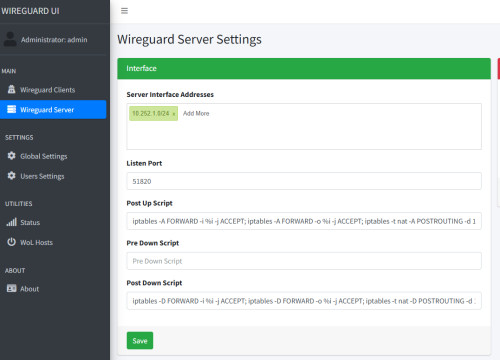
Wireguard Server - Settings
WireGuard post-up and post-down scripts are used to execute commands after starting or before stopping a VPN connection. They enable automated network or system configurations, such as setting firewall rules or adding routing entries that should only be active when the VPN connection is active. I use the following scripts to ensure that the Wireguard Docker container forwards the host's network traffic:
Post Up Script
Post-up script: Configures firewall rules to allow inbound and outbound traffic and mask network packets.
iptables -A FORWARD -i %i -j ACCEPT; iptables -A FORWARD -o %i -j ACCEPT; iptables -t nat -A POSTROUTING -d 192.168.1.0/24 -j MASQUERADEThe IP range 192.168.1.0/24 should of course be adapted to the network or, if necessary, restricted to certain IP addresses.
Post Down Script
Post-down script: Removes the previously set firewall rules.
iptables -D FORWARD -i %i -j ACCEPT; iptables -D FORWARD -o %i -j ACCEPT; iptables -t nat -D POSTROUTING -d 192.168.1.0/24 -j MASQUERADEThe IP range should be set analogous to the post-up script.
Conclusion
WireGuard simplifies the management and protection of networks through the use of Docker containers for VPN use. With the combination of a WireGuard container and the user-friendly WireGuard UI integrated via the Docker Compose configuration, network traffic is handled securely and efficiently, with post-up and post-down scripts contributing to the dynamic adjustment of firewall and routing settings.
 ({{pro_count}})
({{pro_count}})
{{percentage}} % positive
 ({{con_count}})
({{con_count}})