cmd Portscan - Test devices on the network for their services.
Network devices use specific network ports for communication. As an example, port 80 or 443 is used to call up a web page of a web server. In order to establish a connection with a web server, it listens on the corresponding port, in the case of a web server on 443. Theoretically, any port could be used by the web server operator for establishing a connection, nevertheless, port numbers are standardized and certain numbers should be used for certain protocols, such as port 80 for unencrypted web server access: http and 443 for encrypted web server access: https.
Aim of this article
query specific devices over the network,whether these answer to certain network ports
Effort
Reading time: approx. 4 MinutesPrerequisite
Windows-PC in the networkThe tool for network scans: Nmap
With the help of the command line tool Nmap, among other things, ports can be scanned very easily. Nmap can be downloaded free of charge from the manufacturer's site: nmap.org/download.html and is also available for Windows in addition to Linux. For Windows, the .zip archive can be downloaded, extracted and started without installation, in addition in the prompt:
To scan all ports of the IP address 192.168.1.5, the following command can be used after changing to the directory with the unpacked nmap files (cd folder name):
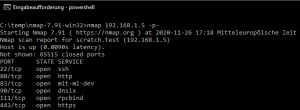
nmap 192.168.1.5 -p-Output:
cd C:\temp\nmap-7.91-win32
C:\temp\nmap-7.91-win32>nmap 192.168.1.5 -p-
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-26 17:18 Mitteleuropäische Zeit
Nmap scan report for scratch.test (192.168.1.5)
Host is up (0.0090s latency).
Not shown: 65515 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
83/tcp open mit-ml-dev
90/tcp open dnsix
111/tcp open rpcbind
443/tcp open https
3000/tcp open ppp
3001/tcp open nessus
3306/tcp open mysql
5983/tcp open unknown
6379/tcp open redis
6380/tcp open unknown
8081/tcp open blackice-icecap
8082/tcp open blackice-alerts
8086/tcp open d-s-n
8123/tcp open polipo
9081/tcp open cisco-aqos
9082/tcp open unknown
40799/tcp open unknown
54327/tcp open unknown
MAC Address: 00:00:xx:xx:xx:xx (ASRock Incorporation)
Nmap done: 1 IP address (1 host up) scanned in 79.68 secondsThe scanned device is my NAS, on which I have installed all kinds of services. In addition to known ports, unknown ports are also displayed. The unknown ports are different services where I used arbitrary port numbers. The used port number is not a guarantee that the protocol used is the one that should be used according to the standard. The command can also be used to test a server on the Internet for its services.
Windows integrated: PowerShell
Alternatively, although much slower, Windows PowerShell can also be used for the port scan:
Net.Sockets.TcpClient instead of Test-NetConnection
Test-NetConnection is nice to check a port, a bit faster is the test via Net.Sockets.TcpClient. Here is an example to scan the first 1024 ports of the IP address 192.168.1.5:
1..1024 | % {write-host ((new-object Net.Sockets.TcpClient).Connect("192.168.1.5",$_)) "Port $_ opened"} 2>$nullLegend:
| 1..1024 | Start and end port for the test |
|---|---|
| 192.168.1.5 | here is an example of the IP address of the computer to be scanned. |
Output:
PS C:\Users>1..1024 | % {write-host ((new-object Net.Sockets.TcpClient).Connect("192.168.1.5",$_)) "Port $_ opened"} 2>$null
Port 22 opened
Port 80 opened
Port 83 opened
Port 90 opened
Port 111 opened
If you have tested the command line, you will notice that the scan is extremely slow. In the example, 1024 of the possible 65535 ports are scanned. This is because one port is tested after the other.
PowerShell >= 7
As of PowerShell version 7, it is possible to use the "-Parallel" parameter in Foreach, which means that several ports can be checked simultaneously: in parallel, which increases the speed enormously. However, Powershell cannot keep up with nmap in terms of performance. In addition, PowerShell 7 is unfortunately not yet available as standard in the current Windows versions and must be installed separately.
If you have installed PowerShell 7, you can use the following command for the portscan:
1..65335 | % -ThrottleLimit 500 -Parallel {write-host ((new-object Net.Sockets.TcpClient).Connect("192.168.1.5",$_)) "Port $_ is open!"} 2>$nullIn older PowerShell versions this is also possible, but not in one line:
PowerShell > 4
PowerShell versions smaller than 7 can map the function via a RunspacePool, as an example for a PowerShell PortScanner I found on GitHub
github.com/BornToBeRoot/PowerShell_IPv4PortScanner/blob/master/Scripts/IPv4PortScan.ps1
Conclusion
If you want to get an overview of the local network, you can list all devices of the local network with simple commands, see: Find IP addresses in the network even if their firewall is enabled. The commands listed here can be used to test individual devices for open ports (services): Nmap.
 ({{pro_count}})
({{pro_count}})
{{percentage}} % positive
 ({{con_count}})
({{con_count}})

